ProSoft Insights / Work Smarter
Keeping your remote access application secure
Keeping your remote access application secure
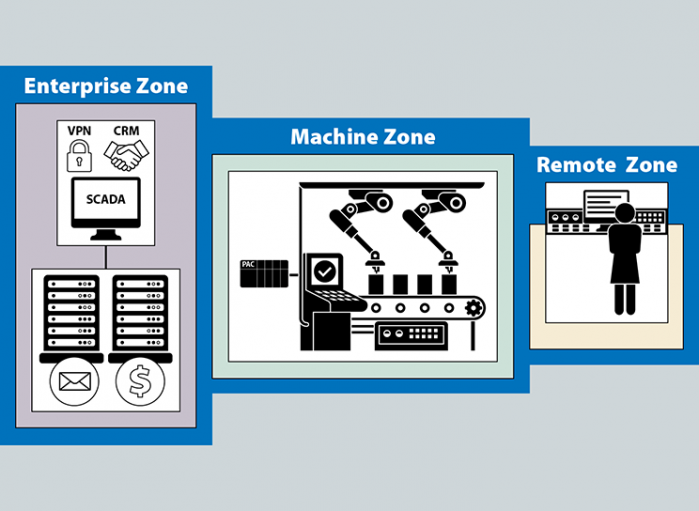
Remote connectivity solutions can bring many benefits that help you optimize resources. A chief concern for any company, however, is the security of their equipment, data, and processes. Remote access systems vary in terms of the types of connections, login security methods, and access levels.
In this white paper, Business Director Keith Blodorn and Strategic Product Manager Vishal Prakash explore the three zones of your operation, and security factors you need to be aware of for each area when considering which remote connectivity solution is best for your application.
Click here to download the white paper!

